Provided by
Ping32
Prevent data leaks in corporate environments.
Meet enterprise software standards.
Prevent data leaks and software piracy.
Enhance IT operations efficiency.
All-In-One, an innovative and integrated solution for endpoint security and data loss prevention.

Internationally recognized ISO 9001 & ISO 27001 dual certification

Driven by security, adhering to EU GDPR data protection standards

Recognized for innovation, featured in multiple global data security reports




Ping32 Data Loss Prevention
Solution
Solution
Ping32 offers a unified data security platform with smart encryption, DLP, and real-time threat detection,
enabling enterprise-wide protection to reduce risks and compliance issues.
enabling enterprise-wide protection to reduce risks and compliance issues.
Data Encryption
Data Loss Prevention
User Behavior Analytics
File Encryption
Strong Protect Confidential Data
By encrypting and securing electronic documents, many leakage risks associated with storing core enterprise data in plaintext during production are mitigated.
Explore Now



Document Encryption
Through the encryption algorithm, the files created by the user through the specified controlled program are encrypted in real time without awareness.

Approval Process
Ping32 enhances efficiency by handling user file decryption and outgoing transfer requests through streamlined approval processes.

Secure File Transmission
Encrypt and control the documents that need to be sent out, and specify the permission to use them to prevent the leakage of the documents.
Data Loss Prevention
A unified data-centric platform for full-spectrum protection.
 Identify Sensitive
Identify Sensitive Identify sensitive files; safeguard high-value data.
 File Transfer
File Transfer Enforce strict controls to prevent document leaks.
 Leak Tracking
Leak TrackingReconstruct leaks; alert and trace sources.
 Device Manager
Device ManagerBlock unauthorized devices; secure external access.
 Intelligent Content Recognition Engine
Intelligent Content Recognition Engine
AI-native architecture with ML-powered content scanning tracks
enterprise data activities.
enterprise data activities.
Explore Now


Intelligent Data Classification
Categorizes dynamic and static data by type and sensitivity to support encryption, masking, and auditing across scenarios.

Policy Enforcement & Live Protection
Applies real-time policies for data sharing, printing, and screen capture to prevent unauthorized access and data leakage.

Comprehensive Audit Logging
Captures the full lifecycle of data activity, enabling post-incident traceability and accountability to ensure violations are well-documented and auditable.
User Behavior Analytics
Behavior Monitoring & Risk Auditing
User and Entity Behavior Analytics (UEBA) leverages analytics and machine learning to detect anomalies, provide security insights, and enhance data loss prevention.
Explore Now



Risk Analysis & Alerts
Analyzes user behavior across compliance, data leakage, and audit dimensions, with multi-channel alerting like email notifications.

Comprehensive Activity Auditing
Covers full-endpoint logs and network traces across data leakage scenarios, enabling fine-grained audit capabilities.

Rapid Incident Tracing
Leverages large-scale log correlation for real-time search and visualized root cause analysis of security events.
Ping32 Unified Endpoint Management
Deliver industry-leading endpoint security that comprehensively protects your enterprise.
Application Control
Device Management
Web Activity
O&M Center
Network Security
Network Access Control
Data Loss Prevention Solution
Ping32 provides a smart security platform with encryption, DLP, and threat detection to keep businesses protected and compliant.
File Encryption
By encrypting and securing electronic documents, many leakage risks associated with storing core enterprise data in plaintext during production are mitigated.
Explore Now


Data Loss Prevention
An all-in-one platform for prevention, control, and audit, protecting sensitive data across devices, emails, and users in real time.
Explore Now


User Behavior Analytics
User and Entity Behavior Analytics (UEBA) leverages analytics and machine learning to detect anomalies, provide security insights, and enhance data loss prevention.
Explore Now


Ping32 Unified Endpoint Management
Deliver industry-leading endpoint security that comprehensively protects your enterprise.
Software Compliance Check
Automated inventory, smart piracy detection, full software control—ensuring compliance and reducing risk.

Peripheral Device Control
Automatically authorizes USBs with matched read/write rights; blocks ports and logs alerts for unauthorized devices.

Network Behavior Management
Effectively manage employee internet activities to minimize risks, protect sensitive data, and enhance overall productivity.

O&M Center
Built-in remote support ensures consistent OS, network, and security settings, reducing risks and ensuring compliance.

Network Security
Analyzes network traffic to detect anomalies, block unauthorized external connections, and prevent data leaks.

FileLink Managed File Transfer
FileLink empowers enterprises to establish an efficient, secure, stable, controllable, and traceable data transmission
channel, enabling high-speed and reliable inter-network file exchange.
channel, enabling high-speed and reliable inter-network file exchange.
Improve Cross-network File Collaboration Efficiency
Help enterprises securely and compliantly transfer files in cross-network environments with network isolation. Ensure transfer traceability and effectively prevent data leaks.
Explore Now


OneNAC Network Access Control
Implements precise port access control to block unauthorized devices and enforce the principle of least privilege.
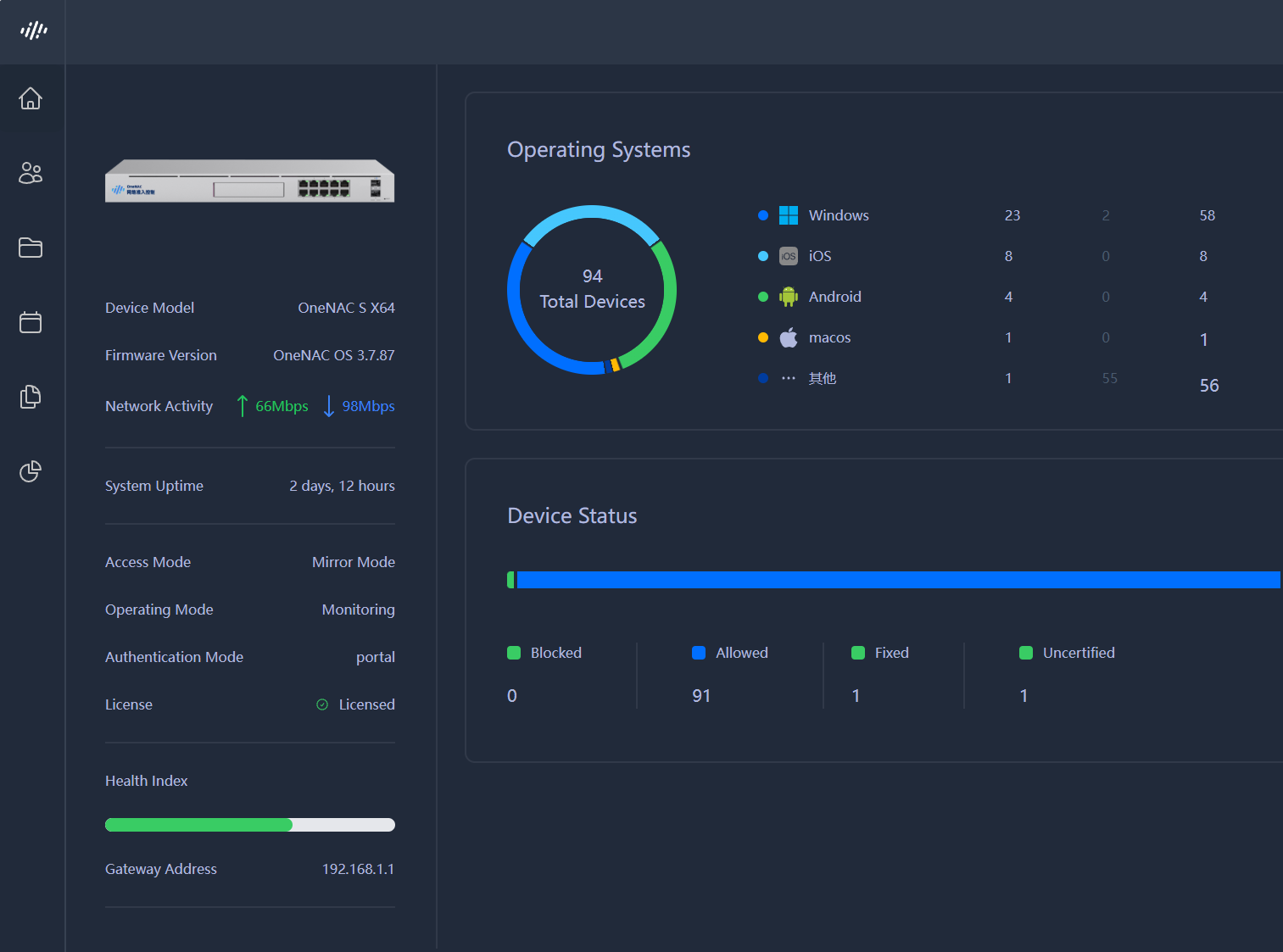

Device Authentication & Authorization
Using 802.1X and multi-factor authentication, enforces precise port control to block unauthorized devices from the network.

Endpoint Compliance Check
Performs health scans before network access, applies scenario-based security baselines, and enables automatic remediation.

Dynamic Access Control
Employs dynamic detection and security policies to manage network access and segment security zones for authenticated users and devices.
Industry Solution
In the era of big data under the "Internet Plus" framework, enterprises must heighten their data security awareness
and implement comprehensive measures to safeguard their information.
and implement comprehensive measures to safeguard their information.


Manufacturing
Unified platform for centralized control.
Ensure terminal data security, protect intellectual property rights, and improve core competitiveness.

Energy
Protect critical infrastructure and data assets.
In line with national information security related policies and standards.

Internet
Expand the leading IT security platform.
Perfect data life cycle management, leak tracking, avoid legal business risks.

Financial
Ensure compliant, efficient financial transactions.
In line with national information security related policies and standards.

Healthcare
Secure digital innovation and medical IoT.
To meet the complex environment of leak prevention, improve public trust.

State-owned
Enhance data security management.
Enhancing the Development of a Data Security Management System.

Industry Solution
In the "Internet Plus" era, enterprises must strengthen data security awareness and take comprehensive protection measures.
Manufacturing
Ensure terminal data security, protect intellectual property rights, and improve core competitiveness.
Internet
Perfect data life cycle management, leak tracking, avoid legal business risks.
Financial
In line with national information security related policies and standards.
Healthcare
To meet the complex environment of leak prevention, improve public trust.
Energy
In line with national information security related policies and standards.
State-owned
Enhancing the Development of a Data Security Management System.
Keep Exploring
Let's Get Started
Contact our expert sales team to learn more about NSecsoft platform and solutions.
Start a free trial or Book a demo





 Contact
Contact





























































































 Contact Us
Contact Us




