Docs
Ping32
Ping32 provides comprehensive solutions for enterprises, including core data encryption, data leakage prevention, endpoint desktop management, software compliance management, and remote operation and maintenance.

Download
Please contact the staff to obtain the latest product installation package, Contact Us.
Hardware Requirements
Ping32 is designed based on a C/S architecture, mainly divided into client, server program, and console modules. The client is deployed on the managed computers, the console is installed on the administrator’s computer, and the server program needs to be deployed on a stable and secure computer to store system management policies and the data reported by the client, and to issue management policies to client computers.
Network Requirements
Ping32 is based on the TCP/IP network architecture and can flexibly expand from the local network to remote networks and offsite networks. Remote computers can also connect to the server through a virtual private network (VPN) or the Internet to achieve centralized management of large-scale complex networks. The console can also connect to offsite servers through the Internet, enabling remote control of branch offices. Real-time monitoring requires a network bandwidth of at least 100KB/S.
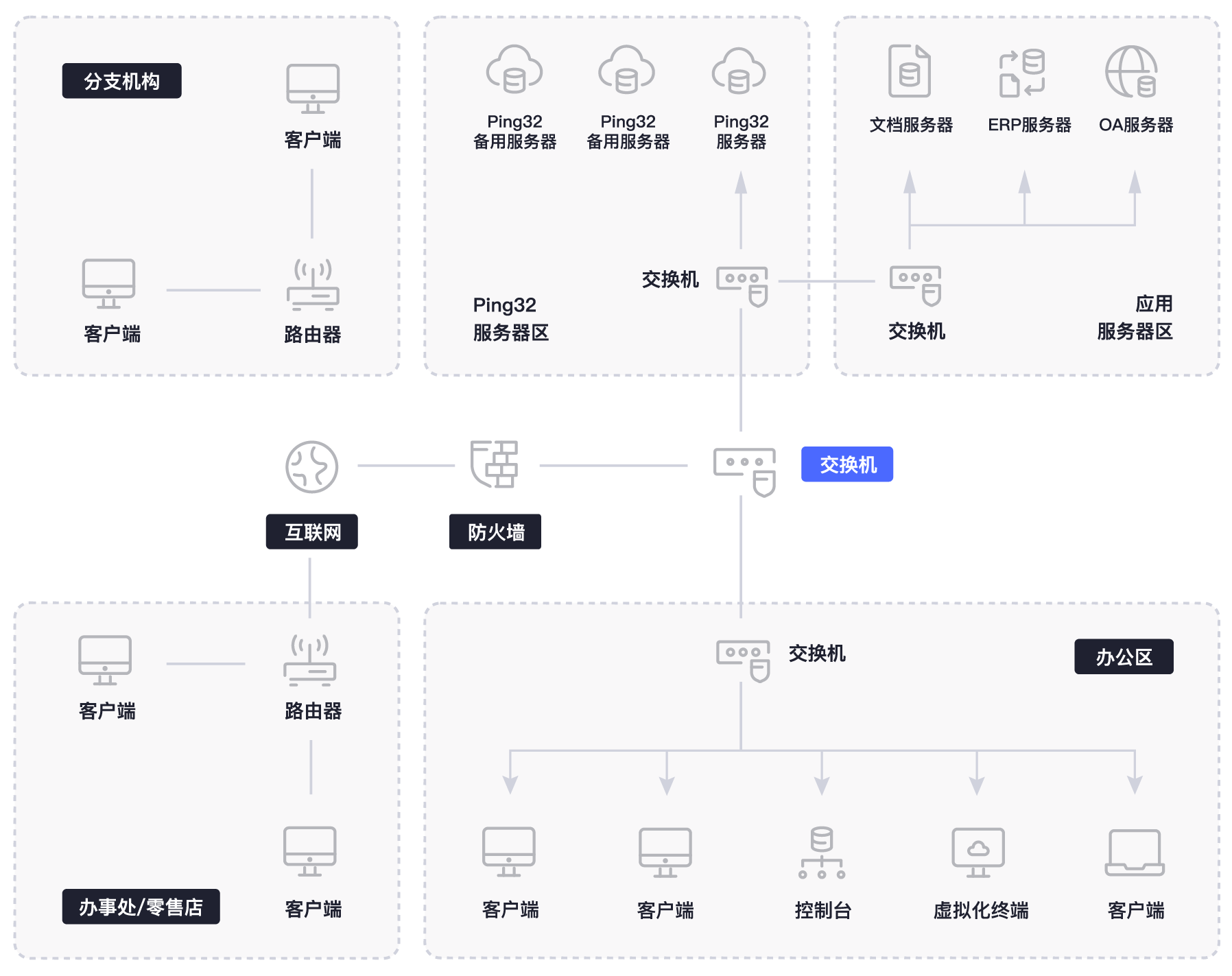
Product Architecture
Before installation, it is recommended to close other applications, including antivirus software, to avoid interference with the normal installation. During the installation process, you can customize the installation path or select installation components according to your needs:
- Console: The management platform provided for administrators. Through the management platform, you can connect to the specified server to manage the endpoints. Multiple consoles can be installed as needed, and different administrator roles can log into the management platform.
- Server: Integrates a high-performance database where endpoint information and audit records are uploaded to the server. Typically, an enterprise only needs to install one server engine.
- Client: Installed on the managed computers, it executes the management policies set by the administrators, collects various operating data of the computer, and uploads it to the server.
Product Activation
To legally obtain the right to use the software and provide better after-sales service, you need to activate the product when you use it for the first time. After logging in, the activation page will pop up, and you can choose a license for activation. If you do not have a license, please contact the official sales staff.
APP
Additionally, you can use the Ping32 mobile app on your mobile device to handle approval processes and view documents to assist with office work, ensuring timely approvals and improving office efficiency.

 iOS
iOS
 Android
Android
Client installation
After successfully activating the system, the system will prompt to generate the client program installation package. Once generated, you can copy the client installation files to other computers via USB drive, email, etc., for installation. Note that the installation package name cannot be changed arbitrarily; changing the name will prevent the installation package from connecting
 Concept
Concept





